General information
Development
Installation
First unzip the archive, then change to the corresponding directory
./configure
make
See the 'Requirements' section.
Requirements
libsrtp and libipq are necessary to run NF_SRTP.
libsrtp :
This program was built from the libsrtp
API : http://srtp.sourceforge.net/srtp.html
The libsrtp package must
be installed on your system. The configure script will look for libsrtp
headers and library in standard directories and in /usr/local/srtp.
Set the srtp_dir variable
along with 'configure' to specify another directory
for the libsrtp package.
In this example, we specify the main libsrtp directory as /local/srtp :
[host]$./configure srtp_dir=/local/srtp/
libipq :
Taken from iptables/netfilter : http://www.netfilter.org.
Usage example
As an example, we run David A. McGrew's rtpw testing program (libsrtp based) on two hosts. The sending host sends an SRTP encrypted and authenticated stream to the receiving one, which runs rtpw without any security service.
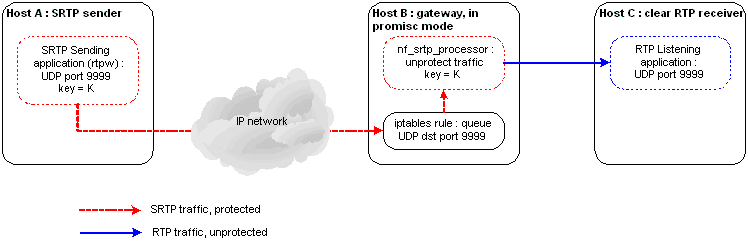
Fig 1 : SRTP stream processed by an intermediate gateway
As we did not ask for any security service on the receiving side through
rtpw,
the nf_srtp_processor program
will provide it. It is important that the same key is used on both hosts.
We 'greped' it from the rtpw
README file in the following examples.
On the receiving host, SRTP packets will be queued (based on UDP destination port) using iptables. nf_srtp_processor will grab/process/reinject these packets to the kernel after before their processing by the running rtpw program on the receiving host.
Example : starting rtpw with confidentiality and message authentication on host 10.1.1.1 :
[10.1.1.1]$set k=c1eec3717da76195bb878578790af71c4ee9f859e197a414a78d5abc7451
[10.1.1.1]$test/rtpw -s -k $k -ea 10.1.1.2 9999
security services: confidentiality message authentication
set master key/salt to C1EEC3717DA76195BB878578790AF71C/4EE9F859E197A414A78D5ABC7451
setting SSRC to 3735928559
sending word: A
sending word: a
sending word: aa
sending word: aal
...
Starting rtpw without any security service on host 10.1.1.2. Security service is handled by nf_srtp_processor :
Queuing packets to userspace with netfilter/iptables:
[10.1.1.2]# iptables -A INPUT
--protocol udp --destination-port 9999 -j QUEUE
Loading IPQ kernel module:
[10.1.1.2]# modprobe ip_queue
Handling packet decryption and authentication check through the nf_srtp_processor
intance. The key must be the same as for the sending rtpw
application :
[10.1.1.2]# set k=c1eec3717da76195bb878578790af71c4ee9f859e197a414a78d5abc7451
[10.1.1.2]# ./nf_srtp_processor -k $k -ea
Starting rtpw without
any security service on the receiving side:
[10.1.1.2]# test/rtpw -r 0.0.0.0
9999
security services: none
19 octets received from SSRC 3735928559 word: A
19 octets received from SSRC 3735928559 word: a
20 octets received from SSRC 3735928559 word: aa
21 octets received from SSRC 3735928559 word: aal
...
Another uage example is given hereafter. NF_SRTP resides on both communicating hosts, along with two clear RTP applications. These applications are not aware of any protection taking place between them.
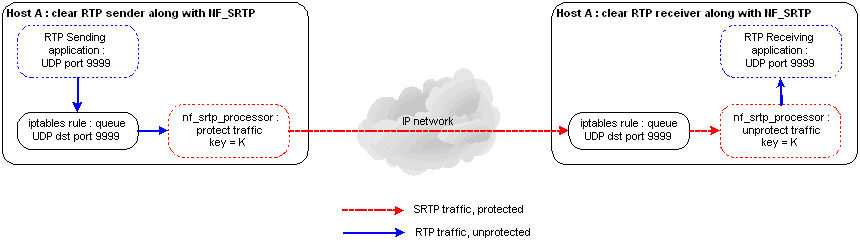
Fig 2 : Two RTP apps, processed locally by two matching NF_SRTP instances
Note (on using rtpw
without security service):
The srtp.c file taken from
the libsrtp package (v
1.3.20) needs to be patched
to allow the use of rtpw
without any security service.
Inserting the following line to the
rtpw.c is sufficient :
policy.key = key;
Here is the diff obtained :
--- rtpw.c.orig 2004-12-30 13:34:36.000000000
+0100
+++ rtpw.c 2004-12-30 13:35:10.000000000 +0100
@@ -308,6 +308,7 @@
* the effect of this policy is to turn off SRTP, so that this
* application is now a vanilla-flavored RTP application.
*/
+ policy.key = key;
policy.ssrc.type = ssrc_specific;
policy.ssrc.value = ssrc;
policy.rtp.cipher_type = NULL_CIPHER;
Note (taken from libsrtp
README file) :
In order to get random 30-byte values for use as key/salt pairs , you
can use the following bash function to format the output of
/dev/random (where that device is available).
function randhex() {
cat /dev/random | od --read-bytes=32 --width=32 -x | awk '{ print $2 $3
$4 $5 $6 $7 $8 $9 $10 $11 $12 $13 $14 $15 $16 }'
}